OAuth 2.0
Introduction to OAuth 2.0
OAuth 2.0 is the industry-standard protocol for authorization, playing a crucial role in securing access to web resources and services. It enables third-party applications to obtain limited access to a web service, operating on behalf of the user. Originating from the need to eliminate the risk associated with sharing password credentials, OAuth 2.0 was designed to provide a more secure and efficient method for granting access. It follows the specifications outlined in RFC 6749, laying the foundation for modern access control in web applications and services.
OAuth 2.0 Authorization Flow
OAuth 2.0 introduces several "grant types" – methods through which an application can obtain authorization. Each grant type is designed for a specific use case, ranging from web applications accessing server-side resources to devices without a browser. However, due to security best practices outlined in the "OAuth 2.0 Security Best Current Practice" guidelines, not all grant types are recommended. This article focuses on the Authorization Code Grant, which is particularly suited for clients capable of interacting with the resource owner's user-agent (typically a web browser) while capable of receiving incoming requests from the [authorization server].
Authorization Code Grant Flow
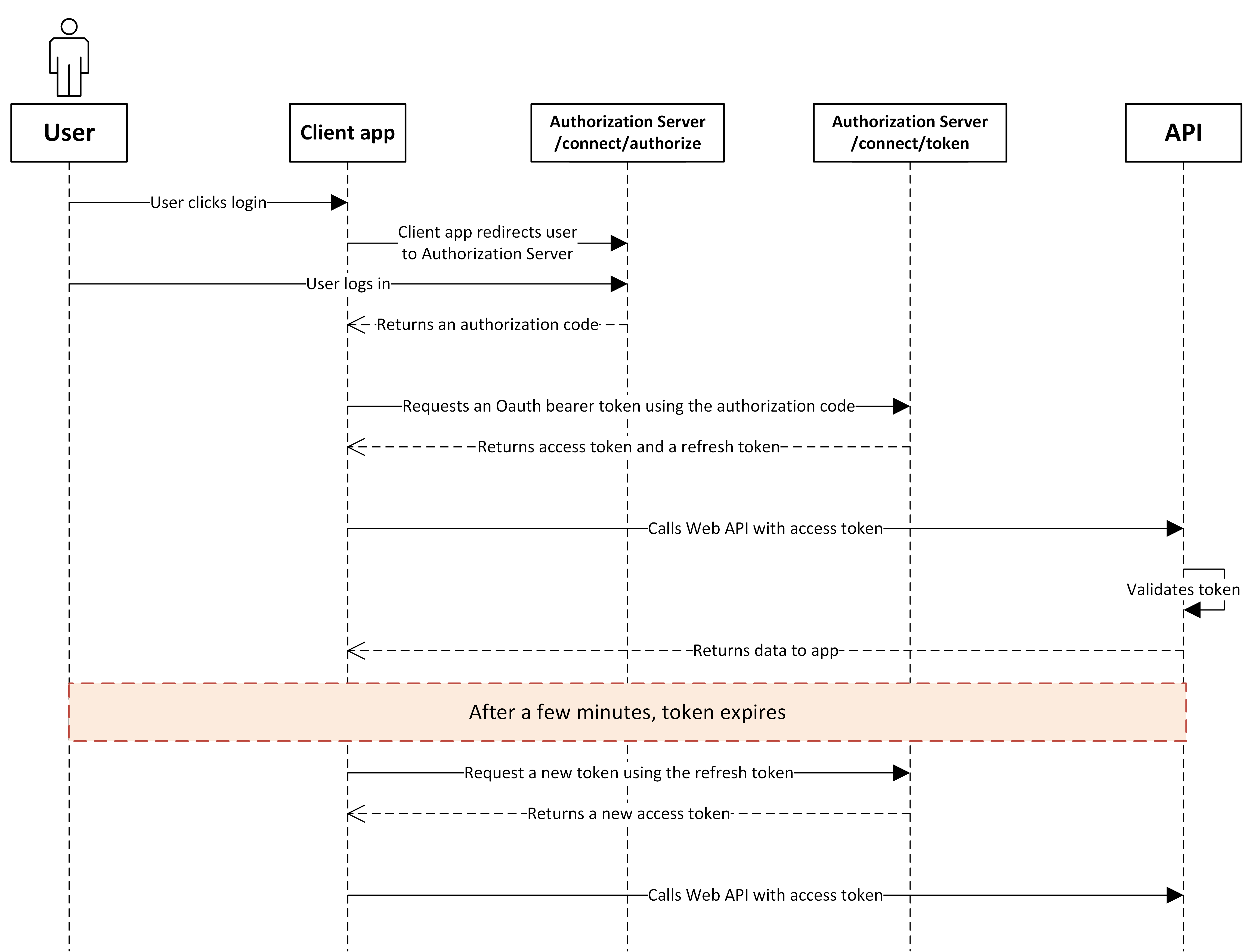
The Authorization Code Grant flow is a two-step process designed to securely exchange an authorization code for an access token. This flow is detailed in RFC 6749 and is as follows:
Authorization Request: The client redirects the user to the authorization server, requesting an authorization code. This step usually involves authentication of the user and obtaining their consent.
Authorization Response: If the user authenticates successfully and grants consent, the authorization server redirects the user back to the client with an authorization code in the query string.
Token Request: The client then requests an access token from the authorization server's token endpoint by including the authorization code received in the previous step.
Token Response: The authorization server authenticates the client, validates the authorization code, and responds with an access token (and optionally a refresh token).
This flow is deemed secure for confidential clients, as credentials are not exposed to the user-agent, and the access token is transmitted directly to the client without passing through the user's web browser.
Clients and Scopes in OAuth 2.0
In OAuth 2.0 terminology, a "client" (e.g. the PERCEIVE portal) refers to the application requesting access to the user's account. Clients are registered with the authorization server, obtaining credentials (client ID and secret) used to identify themselves during the authorization process.
"Scopes" are another pivotal concept in OAuth 2.0, defining the extent of access that the application is requesting. Scopes allow the resource owner (user) to grant permission for specific types of access, such as reading emails or accessing files. This mechanism ensures that applications only receive the permissions necessary for their function, adhering to the principle of least privilege.
Security Considerations
OAuth 2.0 represents a foundational shift in web security, offering a standardized and secure approach to authorizing access to web resources. By following the RFC 6749 standard and adhering to best security practices, OAuth 2.0 facilitates secure, efficient, and flexible authorization mechanisms suitable for a wide range of applications. It's important to note that while OAuth 2.0 significantly enhances security, it must be implemented correctly, considering the latest security best practices and recommendations. For specific security considerations and best practices, refer to the Security Considerations article, which dives into securing OAuth 2.0 implementations in your applications.